Detection, Identification and Reporting of Software Vulnerabilities that threaten security
Network and endpoint security is no longer just the domain of corporate IT security teams. Today’s security initiatives are far-reaching and often involve many different organizational functions, systems, networks and geographic operations.
IT Asset Management (ITAM) and Software Asset Management (SAM) programs can provide essential input to security initiatives since they have a tremendous amount of up-to-date information about installed hardware and software at their fingertips.
Now your ITAM and SAM programs can help reduce your organization’s degree of risk even further with Eracent’s Software Vulnerability Manager. This powerful functionality is based on standardized data that is continuously gathered by the National Institute of Standards and Technology (NIST). Several times a day, NIST updates a database of all known vulnerabilities that exist in commercial IT hardware and software products. Within hours of the NIST database being updated, Eracent maps this new vulnerability data to product records in both the SCANMAN™ software recognition library and the IT-Pedia® IT Product Data Library.
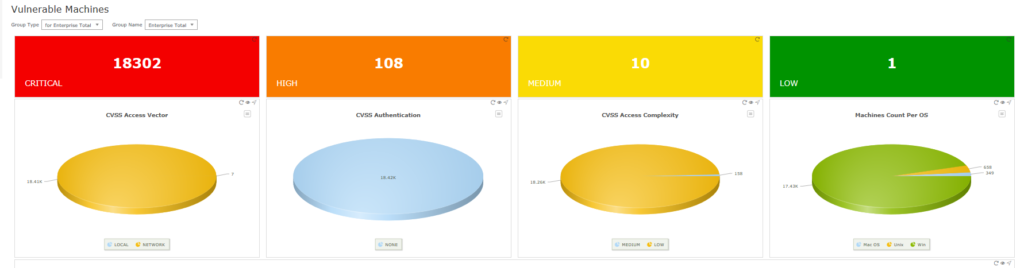
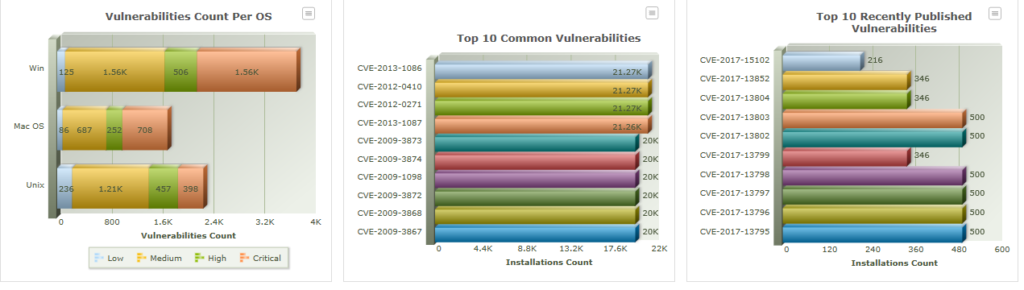
As a result, ITMC Discovery™ can quickly identify any installed products that have known vulnerabilities. You can see any potential threats and software that needs to be patched, updated or replaced throughout your network environment.
Out-of-the box reports include:
- Summary dashboards with drill-down capabilities
- Vulnerabilities by individual machine, OS, publisher or product
- Impact Type and Level of Criticality
- Installation counts by vulnerability
Not only can you see if a currently installed application has a known vulnerability, but through IT-Pedia, you can also see if new products or versions that you are considering purchasing or installing may also have a known issue.
Being able to quickly identify any machines or installed software that may be a threat is just one aspect of a broader network security initiative, but it can be a very effective piece of the puzzle.
Verifying Standard Images
ITMC Discovery provides another level of protection by ensuring that your environment is fully covered from a security standpoint. Discovery scans detect the presence of any installed anti-virus software and can indicate unprotected machines. Scans can also check for all applicable Windows patches and can report on any machines that deviate from the most current, up-to-date standard image. This provides another layer of defense against vulnerabilities.
Additional Protection: Software End-of-Life Data
Another element in preventing unwanted network intrusion is software end-of-life (EOL) and end-of-support (EOS) data.
If a product or version is still installed when its end-of-life or end-of-support date is reached, it creates a security risk since it will not be possible to get a patch or fix from the publisher. Having EOL and EOS data readily available makes it easier to plan for refresh cycles and avoid potential software-based threats to endpoint and network security.
Publishers and manufacturers often provide end-of-life and end-of support dates well in advance, but they are not always easy to find. The dates may be in a PDF on a support website, in a letter or email sent to someone in your organization who may not understand the importance of this information, or they could be published elsewhere. They are not always obvious and it’s not difficult to overlook these critical dates that require action.
IT-Pedia consolidates this end-of life and end-of-support data and puts it front and center. Eracent continuously gathers and adds EOL and EOS dates for hardware and software products to IT-Pedia, where it is available for automated updates on a daily basis. This information can be easily shared with ITSM, ITAM and other systems.